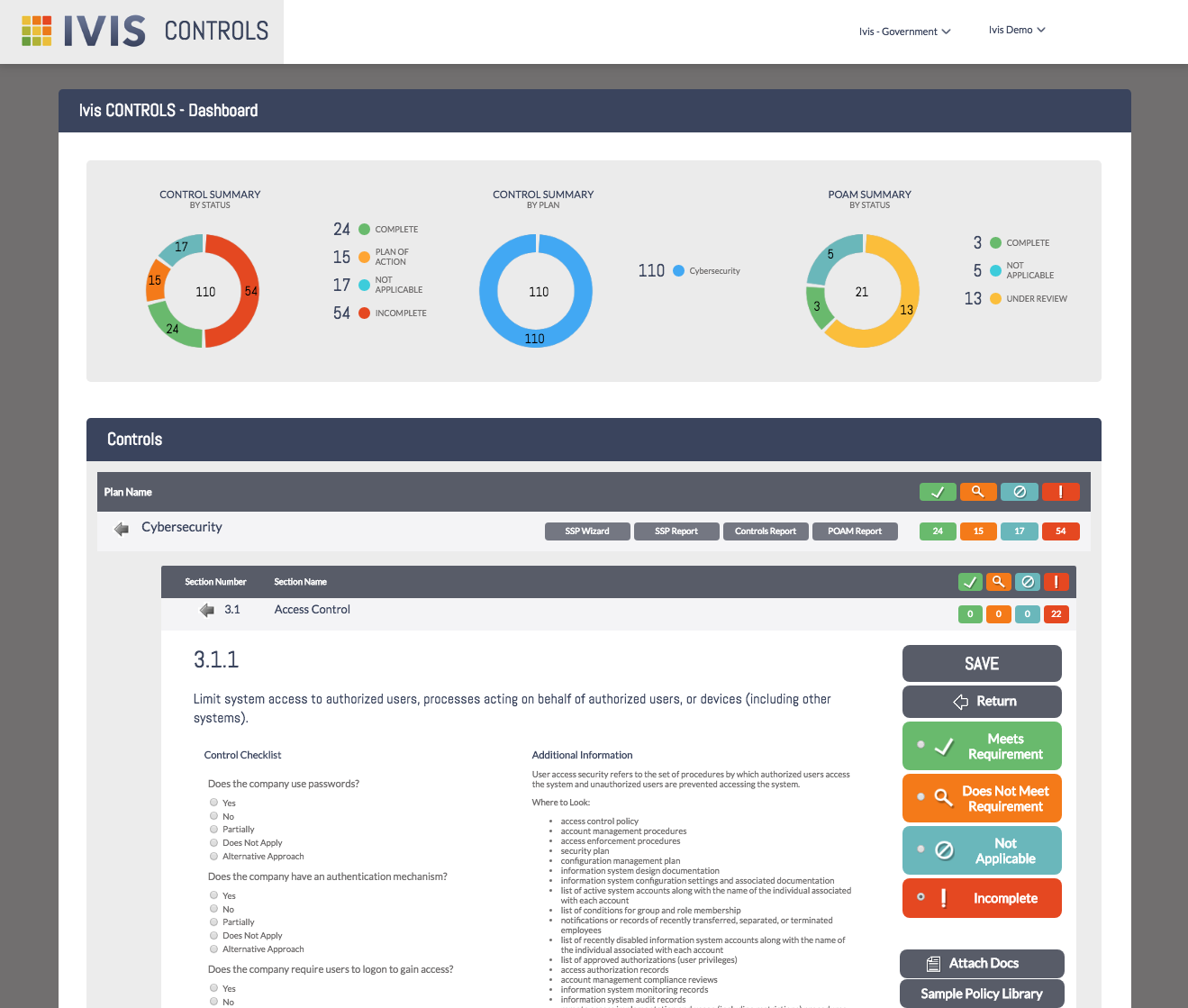
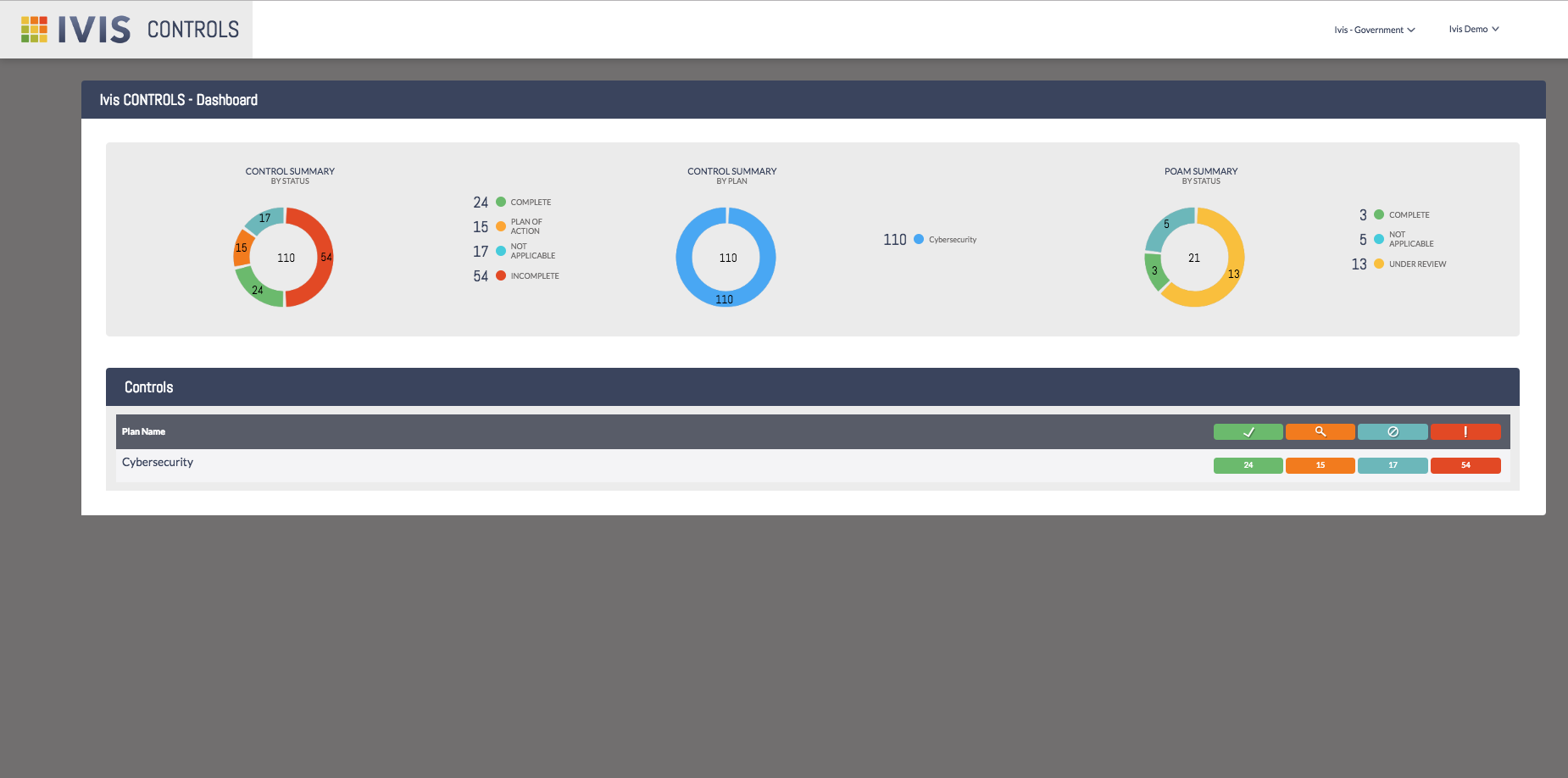
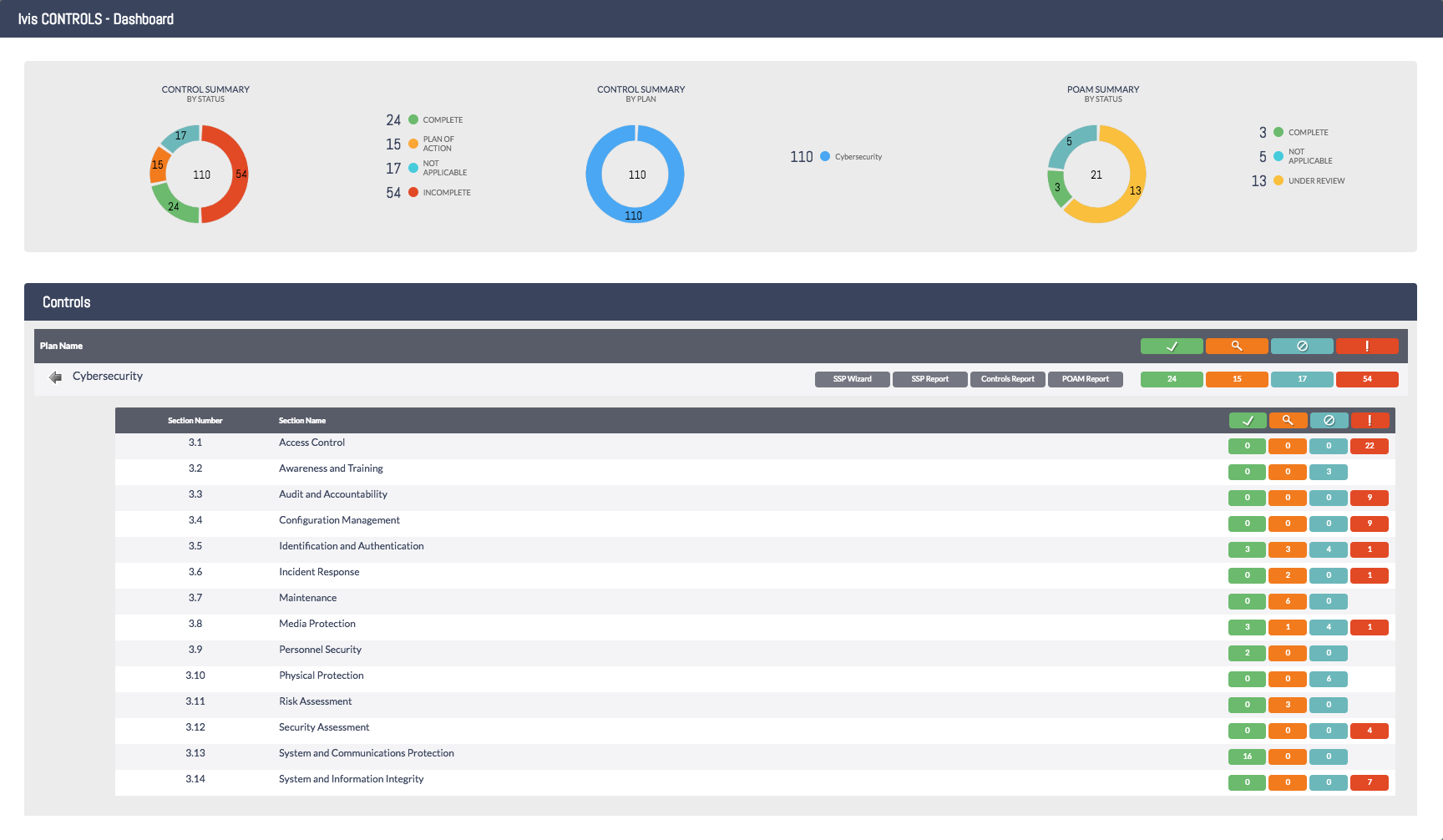
The Ivis CONTROLS Dashboard gives you a quick overview of all core elements you have installed in your instance. Right now we have only cybersecurity and we can quickly see that we have 24 completed, 15 controls with a POAM, 17 not applicable controls, and 54 incomplete controls. We can also see the POAM summaries; 3 are complete, 5 are not applicable and 23 are under review.
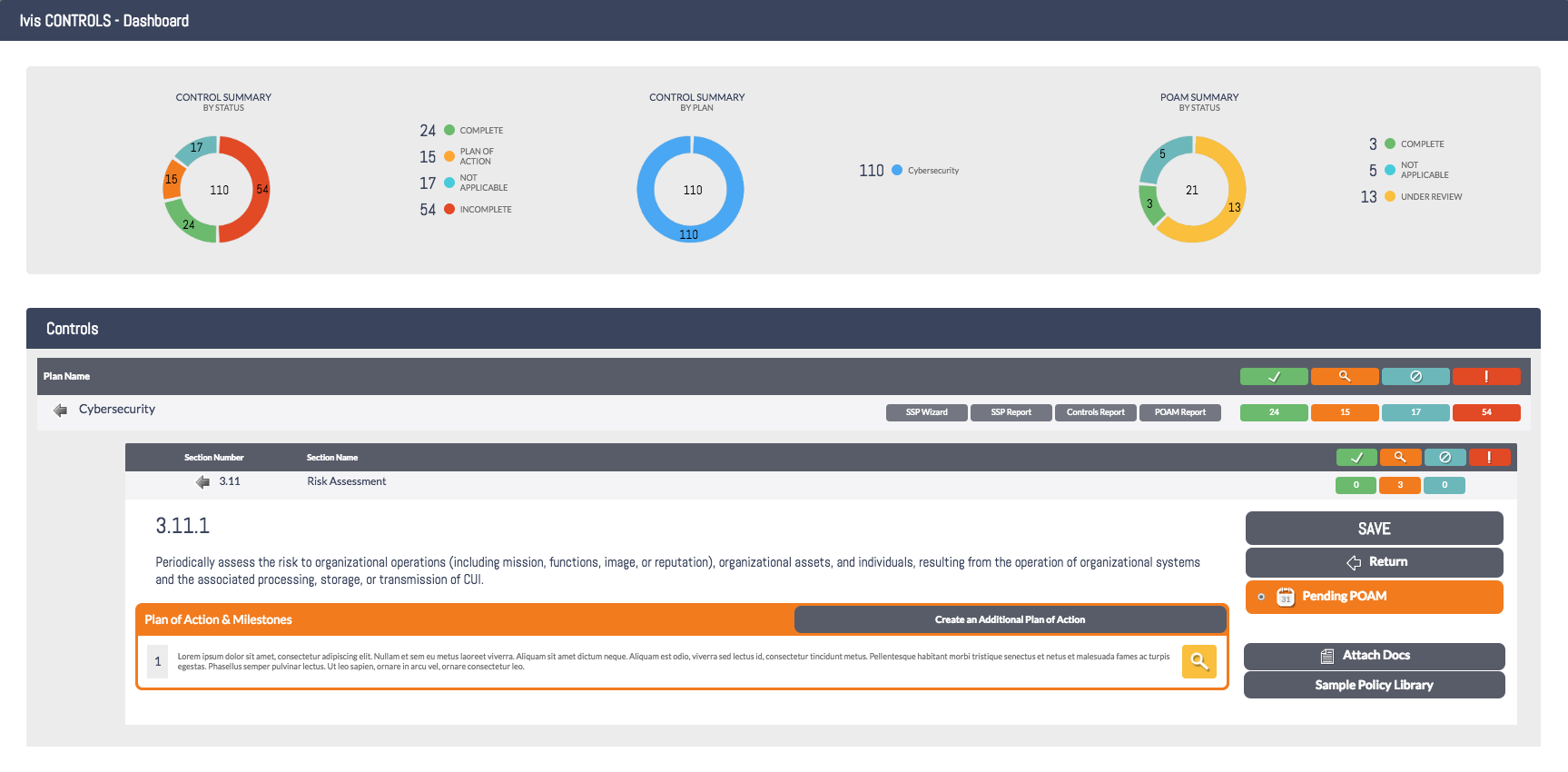
Here you can see the fourteen different NIST 800-171 control families as well as the individual statuses of those controls. The green checkmark represents completed controls. The orange magnify glass shows if the control has a POAM associated. The blue no symbol means not applicable and the red exclamation point is for an incomplete control, or a control with a completed/not applicable POAM that needs further attention.
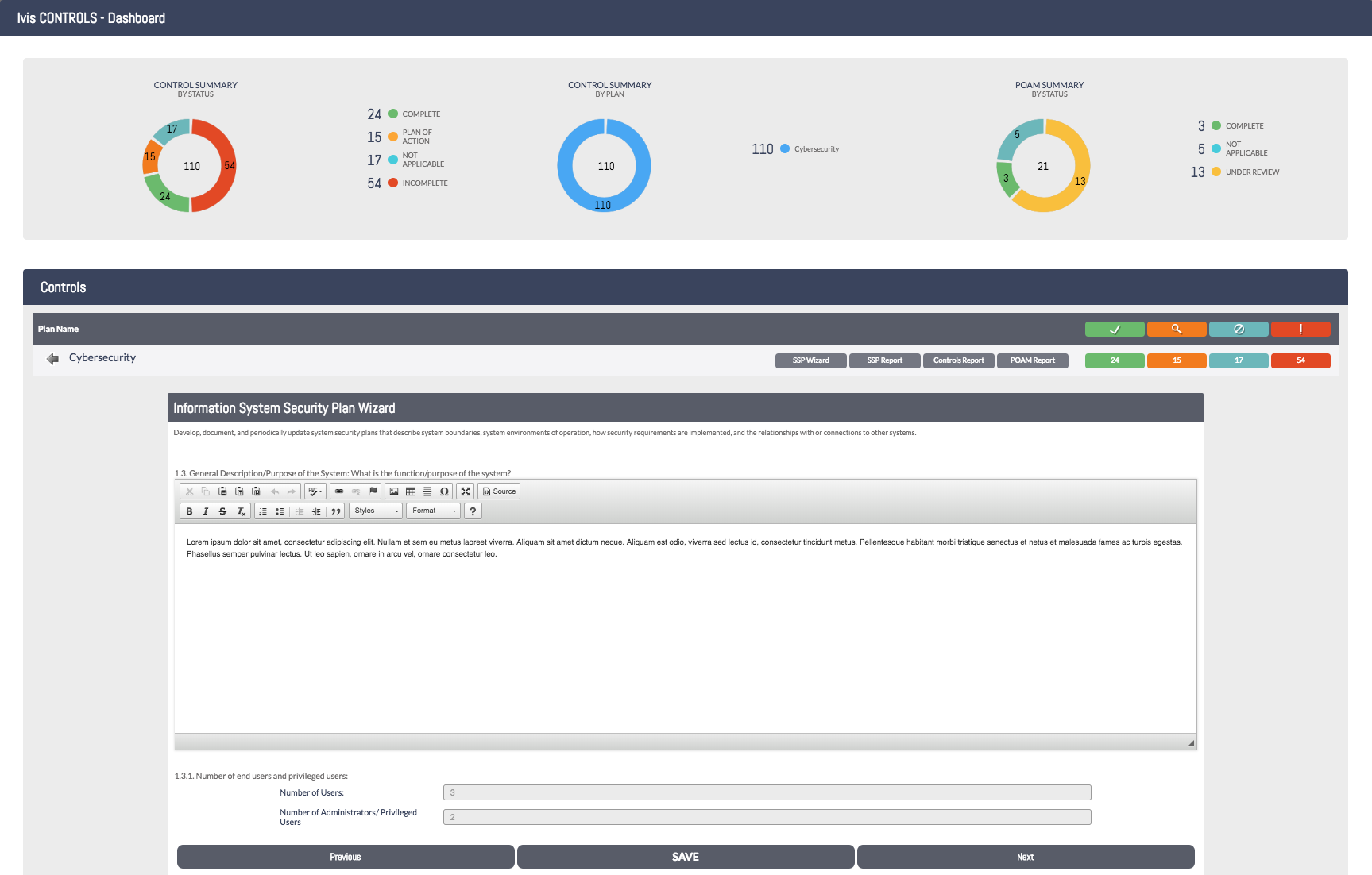
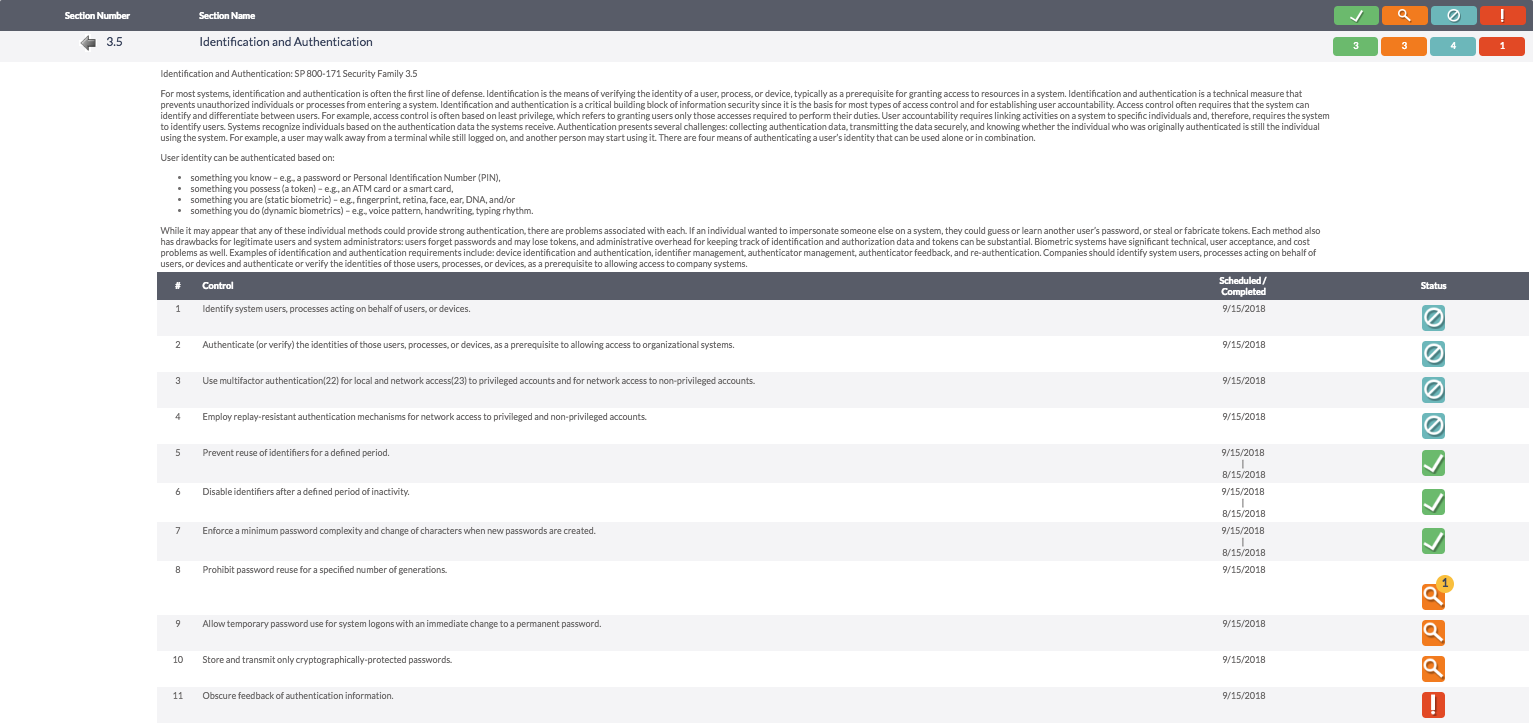
This is the individual control family view. Here you can see the 3.5 – Identification and Authentication family and listed below is a description of that section. In this view, you will be able to see the statuses of all the individual controls as well as the scheduled and completed dates.
| Americans with Disabilities Act | Data Breach Laws | Harrassment | Payment Card Industry Security Standard (PCI DSS) |
| Anti-Boycott | Discrimination | Health Insurance Portability and Accountability Act | Personal Conflicts of Interest (Government Support Services) |
| Anti-Corruption | Economic Espionage Act | Human Trafficking | Personal Identity Verification I-9 Compliance |
| Antitrust | FAR Mandatory Disclosure | Import/Export | Revolving Door |
| Business Ethics Awareness Program | Family and Medical Leave Act | Insider Trading | Sarbanes-Oxley Acts of 2002 |
| Conflict Minerals | Federal Awardee Performance and Integrity Information System (FAPIIS) | NIPSOM - Handling Classified Information | Truthful Cost or Pricing Data |
| Conflicts of Interest | GDPR | Organizational Conflicts of Interest Vetting | Wages and the Fair Labor Standards Act |
| Cybersecurity |
Pricing starts at $. For more information – https://ivis.com/pricing/
| Business Ethics Awareness Program |
| Cybersecurity |
| GDPR |
| Health Insurance Portability and Accountability Act |
| Payment Card Industry Security Standard (PCI DSS) |
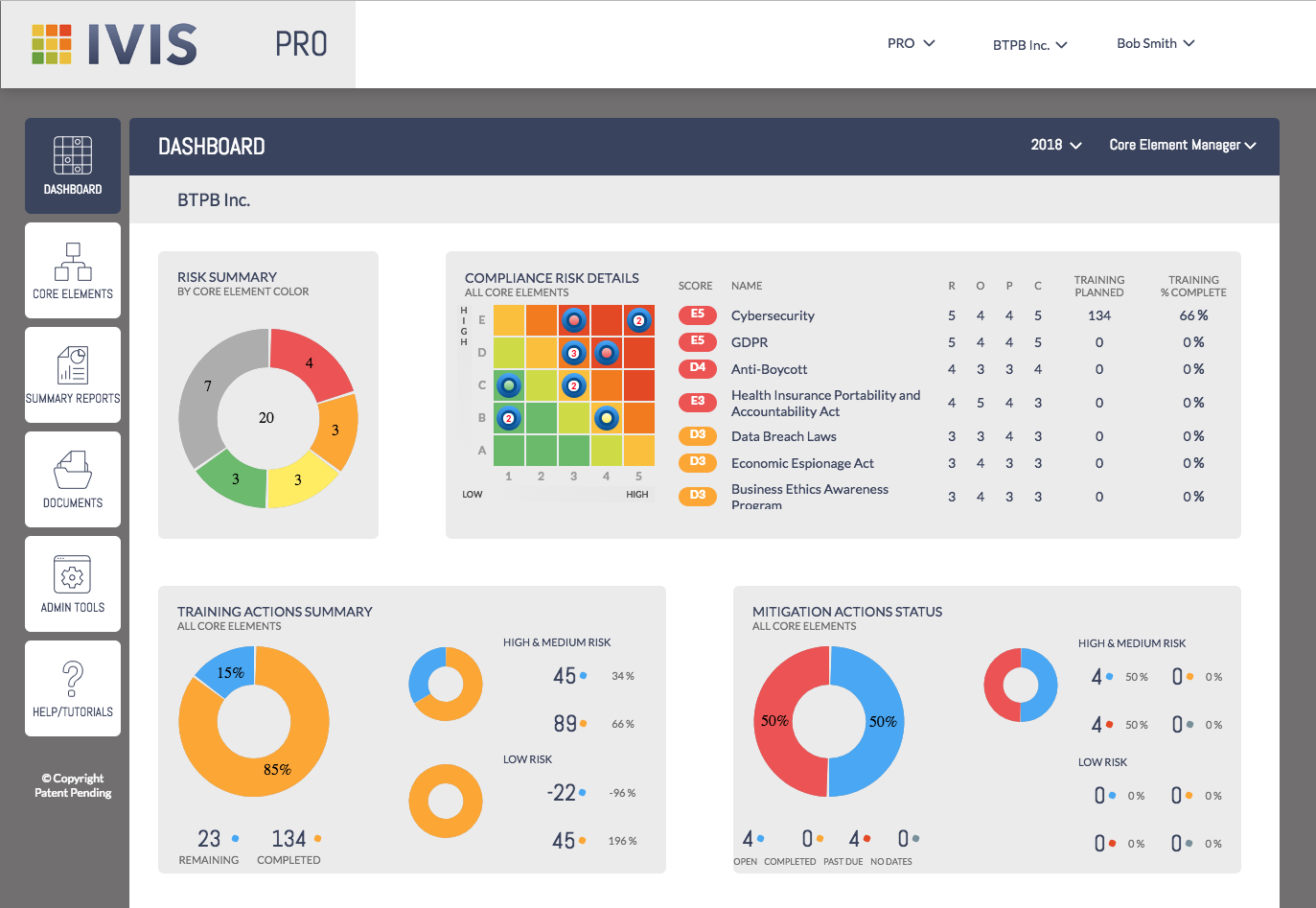
Designed to give users a detailed view of the info they need, at-a-glance. Some of the top features include:
Compliance Risk Details – Program managers can quickly view the current risk ratings, risk assessment scores and training.
Training Summary – Gives your staff the ability to assess the progress of high, medium and low risk training.
Mitigation Status – Allows for the overview of mitigation task status and verification of performance by task and risk level.
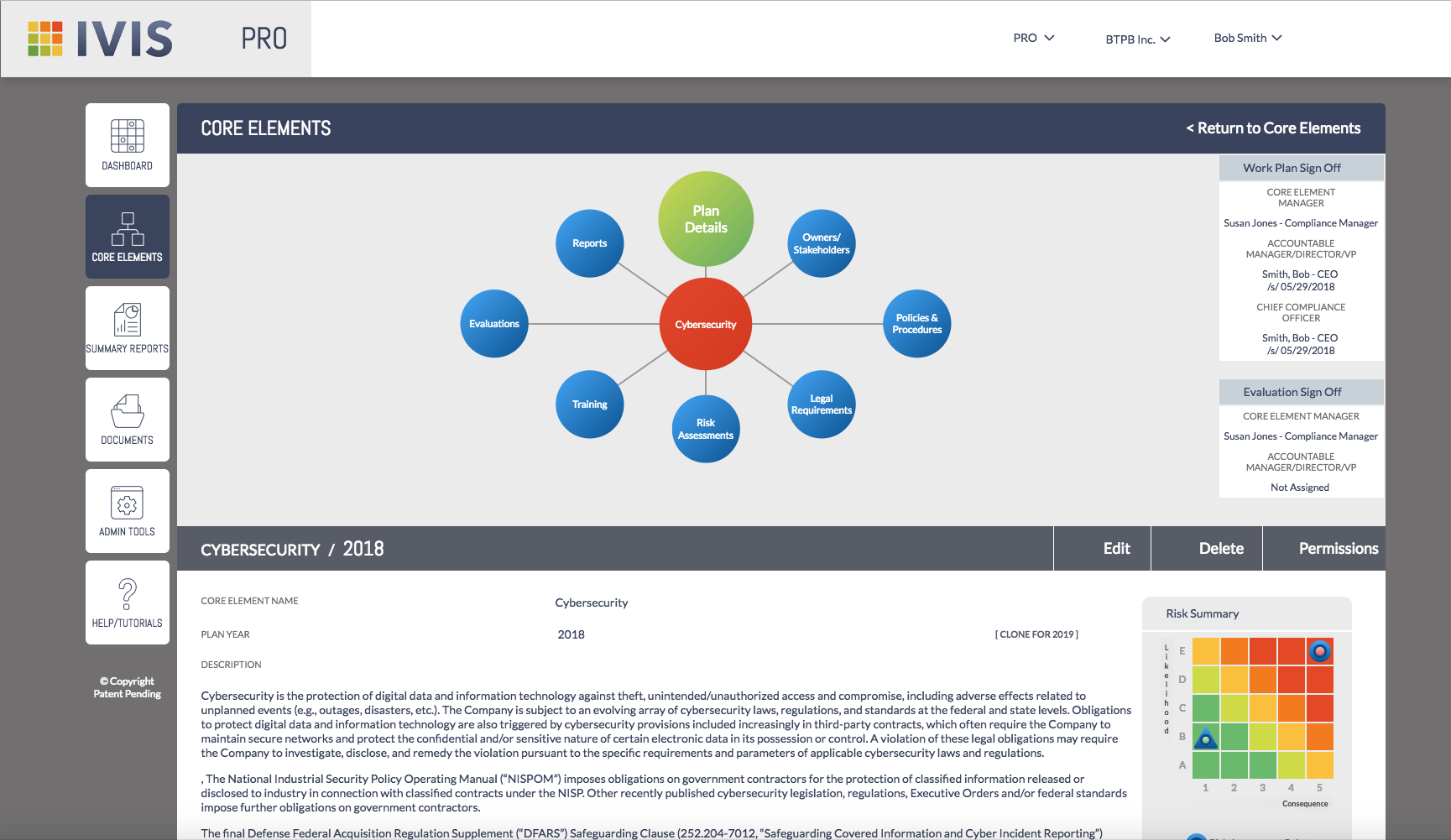
The plan maps out your compliance strategy, process, and goals. The feature gives all users, from the executive suite to front line staff, the core element details: the who, what and how.
Who – Identifies the compliance manager, department accountable, legal team and individuals at risk as associated with the current element.
What – Provides critical details like description, element year and a snapshot of risk assessment.
How – Lists applicable statutes, policies and procedures, communication methods and task status for the current plan in addition to electronic signatures for plan participants.
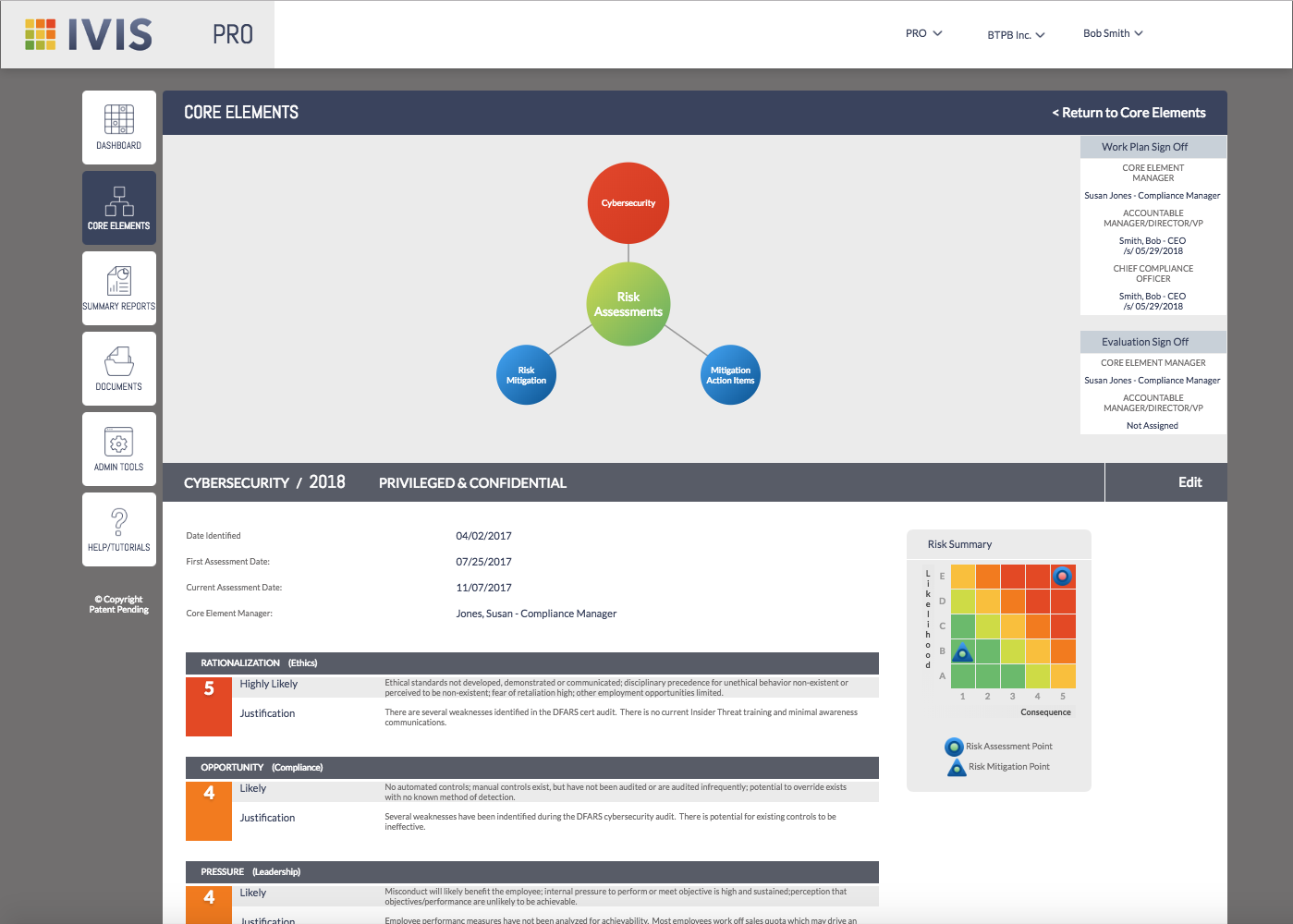
Ivis PRO identifies and exposes areas where your company is vulnerable to risk and fraud
– Incorporates the Fraud Triangle to help you evaluate your organization’s risk and select scores for rationalization, opportunity, pressure and consequence.
– Our assessment process features the ability to enter justification information for each score.
– Easily view risk assessment and mitigation scores on the Ivis Risk Cube.
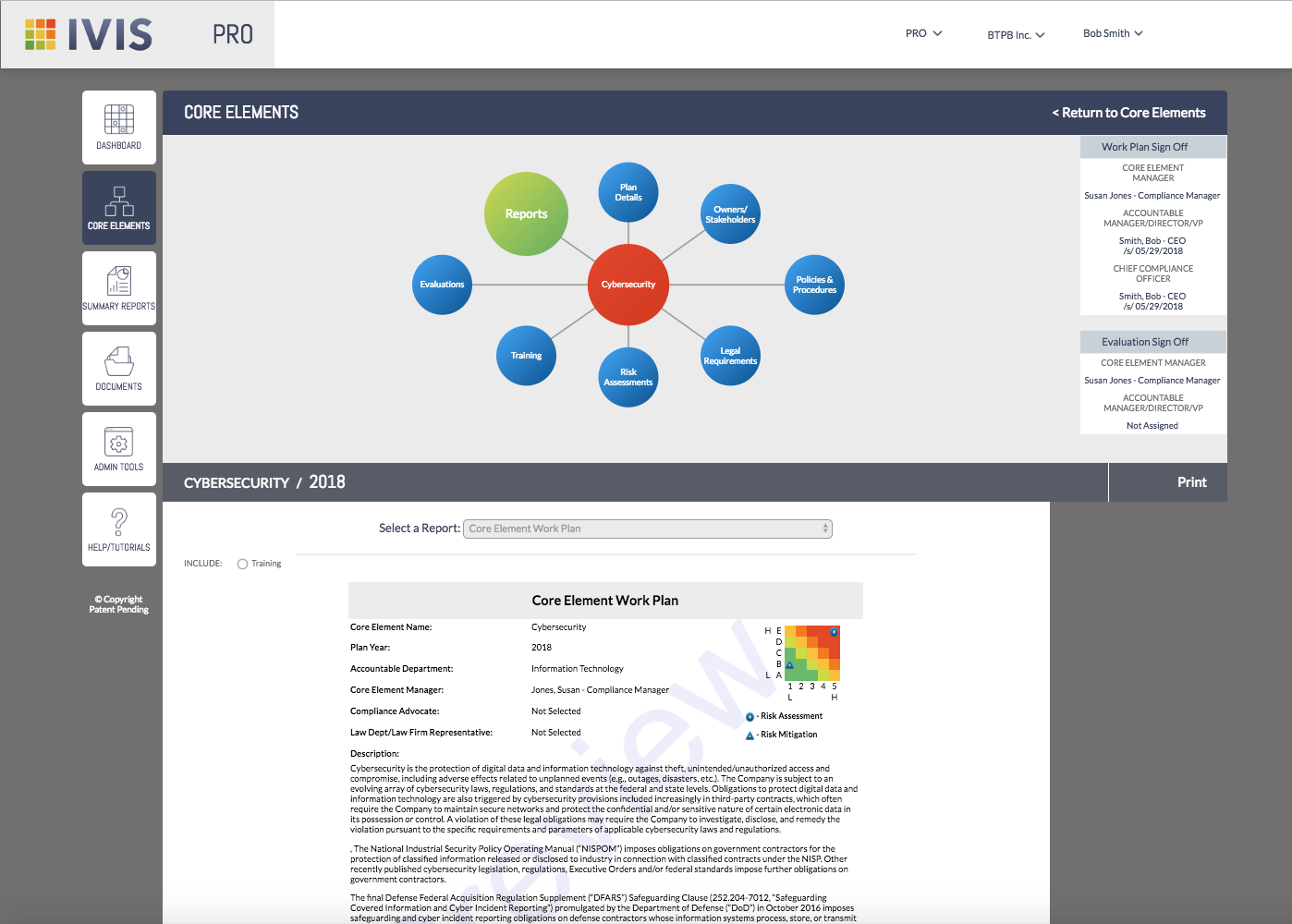
Supports the critical function of reporting, showing proof via an audit trail that risks, fraud, and tasks are being addressed.
– Provides compliance reporting for the entire plan and plan segments.
– Summaries that give you an overview of your organization’s compliance and risk plans.
Pricing starts at $. For more information – https://ivis.com/pricing/
The NIST Cybersecurity Plan Review service takes the trial and error out of the NIST compliance process, reducing expenses, and clarifying path forward for a company. This program is designed for either those organizations that have already built a complete NIST cybersecurity plan and are leveraging the Ivis compliance platform or those who need recommendations on how to complete their plan to put into the Ivis compliance platform. It consists of two primary components.
NIST Cybersecurity Plan Review
A well designed NIST Cybersecurity Compliance Plan increases clarity by providing the most effective direction to bring a company from its current state to achieving and maintaining compliance. Silent Sector’s Plan Review provides an independent opinion to validate your current plan and may offer guidance to improve the plan where necessary.
Plan Recommendations
Some companies will have a plan in place, but may need adjustments in order to be considered viable. Professional recommendations are written alongside the existing plan in the Ivis compliance platform allow for focused effort and the best of resources through the duration of the compliance process.
In an effort to ensure that a company is able to meet and maintains compliance requirements, Silent Sector will perform the following activities related to NIST SP 800-171A.
NIST Cybersecurity Plan Review
Silent Sector will provide the following deliverables:
The following is the estimated timeline for SOW completion. This timeline is subject to change based on unanticipated findings, platform issues, or communication delays. Silent Sector holds the right to start the project in the order it was received.
| Initial Plan Review | Week 1 |
| Recommendations and Verification of Review | Week 2 |
All costs listed below are based on the cope and assumptions included in this Statement of Work
| NIST Cybersecurity Plan Review | $550 |
The NIST Cyber Alignment program takes the trial and error out of the NIST compliance process, reducing expenses, increasing clarity, and paving a clear path forward. This program consists of three primary components.
Gap Analysis – Current Posture to NIST SP 800-171A
Companies will have a clear picture of what is already in place and where they fall short of meeting NIST requirements. This allows for focused effort and the best of resources through the duration of the compliance process.
NIST Alignment Plan Development
Every company differs and therefore requires its own unique strategy to meet and maintain NIST cybersecurity requirements. The NIST Alignment Plan increases clarity by providing the most effective direction to bring a company from its current state to achieving and maintaining compliance. It leverages the Ivis compliance platform for ease of tracking and evidence retention.
Cyber Risk Assessment
A clear understanding of risks and potential attack vectors is the foundation of cybersecurity. Silent Sector provides a clear but detailed analysis of vulnerabilities and the current state of risk.
Silent Sector will provide an independent perspective of cybersecurity vulnerabilities and risks related to network infrastructure and any critical web applications. This allows for the development of a strong security posture, while making the best use of resources.
Conducting the Risk Assessment will:
In an effort to ensure that companies maintain a secure and digital environment, Silent Sector will perform the following cyber risk and NIST SP 800-171A compliance related activities.
Gap Analysis – Current Posture to NIST SP 800-171A
NIST Alignment Plan Development
Cyber Risk Assessment of Network Infrastructure (maximum of 60 hours)
Silent Sector will provide the following deliverables:
The following is the estimated timeline for SOW completion. This timeline is subject to change based on unanticipated findings, platform issues, or communication delays.
| Interviews & Information Collection | Week 1 |
| Analysis and Gap Assessment Development | Week 2 |
| Pre-planning Interviews & NIST Alignment Plan Development | Weeks 3 – 5 |
| Report Delivery, Review, and Discussions | Week 6 |
Please contact Ivis at [email protected]
NIST Gap Analysis & Cybersecurity Plan Development services take the trial and error out of the NIST compliance process, reducing expenses, increasing clarity, and paving a clear path forward. This program is designed for organizations that require a cybersecurity plan to meet NIST requirements and will be utilizing the Ivis compliance platform. This program consists of two primary components.
Gap Analysis – Current Posture to NIST SP 800-171A
Companies will have a detailed understanding of where they fall short of meeting NIST SP 800-171A requirements. Silent Sector will review the existing compliance plan to provide a 3rd party perspective on the status of the plan and assist with identifying shortcomings. This allows for focused effort and the best of resources through the duration of the compliance process.
NIST Cybersecurity Compliance Plan Development
Every company differs and therefore requires its own unique strategy to meet and maintain NIST cybersecurity requirements. The NIST Cybersecurity Compliance Plan will provide a clear path from its current state to achieving and maintaining compliance. This plan will incorporate the use of the Ivis compliance platform.
In an effort to ensure that a company is able to meet and maintains compliance requirements, Silent Sector will perform the following activities related to NIST SP 800-171A.
Gap Analysis – Current Posture to NIST SP 800-171A
NIST Cybersecurity Plan Development
Silent Sector will provide the following deliverables with a maximum time allocation of 40 hours.
The following is the estimated timeline for SOW completion. This timeline is subject to change based on unanticipated findings, platform issues, or communication delays.
| Interviews & Information Collection | Week 1 |
| Analysis and Gap Assessment Development | Week 2 |
| Pre-Planning Interviews & NIST Alignment Plan Development | Weeks 3 – 4 |
| Report Delivery, Review, and Discussions | Weeks 4 – 5 |
Please contact Ivis at [email protected]